Hackers now use double extortion, actively destroy backups, and exploit weak or missing multi-factor authentication (MFA). For law firms, these tactics threaten client trust, compliance obligations, and even day-to-day survival.
This article explores how attackers are exploiting these gaps and what law firms can do today to close them.
Want to know if your firm is vulnerable? Start with a Free IT Assessment today.
The Rise of Double Extortion
Classic ransomware encrypted files and demanded payment for a decryption key. Today, attackers take it further. In a double extortion attack, cybercriminals first steal large amounts of client data, then lock systems. Even if a firm restores operations from backups, hackers threaten to publish or sell the stolen information unless another payment is made.
For law firms, the impact is devastating. Confidential case files, merger documents, medical records, and personal data can all be exposed to the public or dark web.
Example: The attack on Grubman Shire Meiselas & Sacks illustrates the stakes. Hackers demanded a $42 million ransom and, when the firm refused, leaked high-profile celebrity contracts and client data. The damage extended far beyond IT systems and became front-page news.
Backup Systems Under Attack
For years, firms relied on backups as their insurance policy. But ransomware groups now target backups directly. Malware scans networks to find and encrypt connected drives or online storage, leaving firms with nothing to restore.
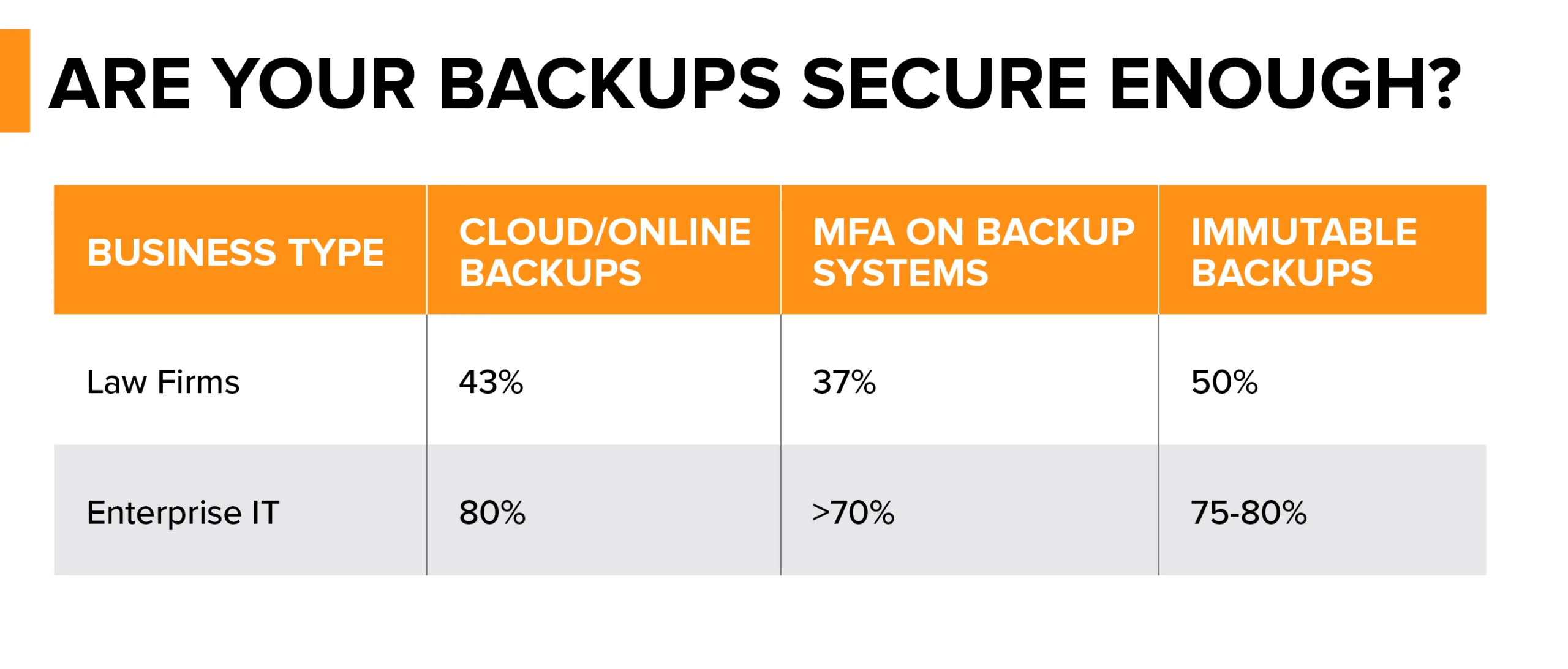
The problem is compounded by weak adoption of best practices:
- Only 43% of law firms use cloud backups.
- Just 37% protect backups with MFA, leaving them vulnerable to stolen credentials.
- Only about 50% of firms report having “immutable” backups that cannot be altered or deleted.
When backups fail, downtime skyrockets, ransom payments become more likely, and the cost of recovery soars.
MFA Gaps and Access Exploits
Multi-factor authentication (MFA) is one of the most effective defenses against unauthorized access. By requiring a code or token in addition to a password, MFA blocks the vast majority of phishing-based intrusions.
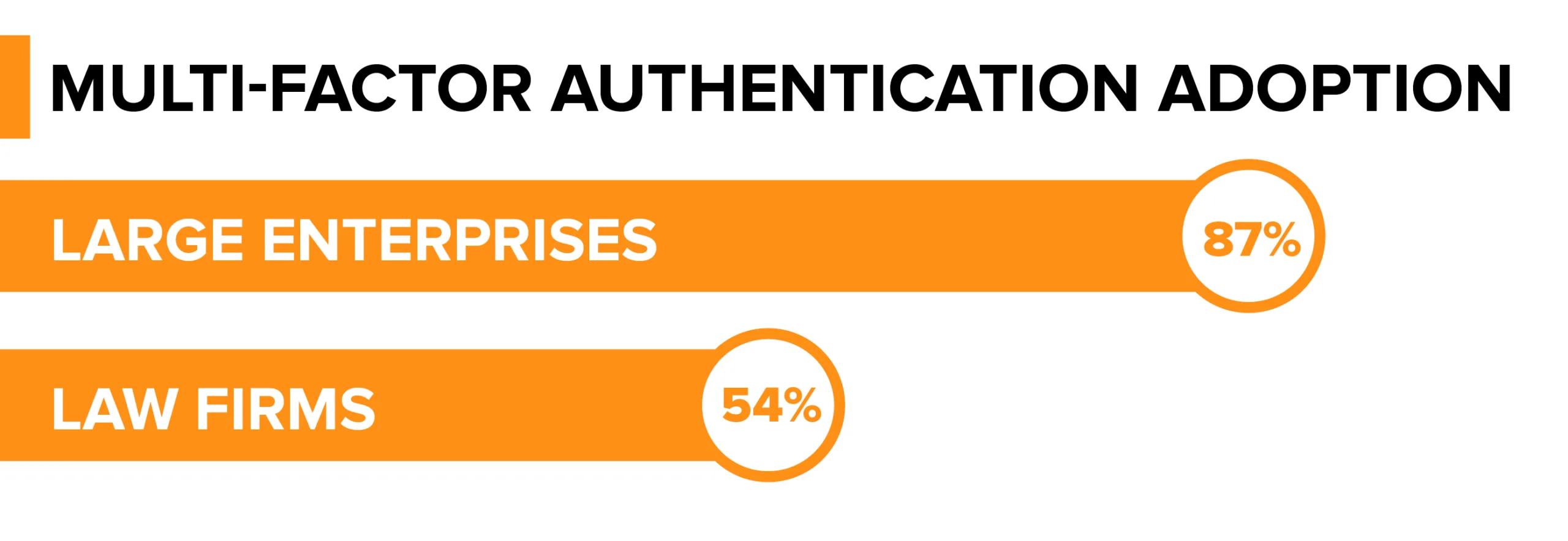
Yet only 54% of law firms report using MFA, compared to 87% of large enterprises. That leaves nearly half of firms open to credential theft, phishing, and brute-force attacks.
Without MFA, attackers who steal or guess a password can move freely through email, case management software, and file servers. Once inside, they can disable security tools, exfiltrate data, and plant ransomware, often without being detected until it is too late.
Social Engineering on the Rise
Technology isn’t the only way attackers infiltrate firms. Social engineering has become a powerful tool, targeting lawyers, paralegals, and administrative staff who may not recognize subtle threats.
- Callback phishing: Attackers send fake emails instructing staff to call a phone number, where a live scammer convinces them to install malware.
- AI-driven phishing: Messages are personalized and convincing, making them harder to detect.
- Vendor compromise: Third-party software or service providers are hacked, as in the MOVEit supply chain attack, and law firms are compromised as collateral damage.
These tactics bypass traditional defenses by exploiting human trust. Without regular training and awareness, even cautious staff can be tricked.
Hackers are evolving. Is your firm keeping up? Schedule your Free IT Assessment today.

How Law Firms Can Close the Gaps
The tactics may be evolving, but law firms can take clear steps to reduce their exposure:
- Implement MFA firmwide. Apply it to email, VPNs, backups, and case management systems.
- Secure and test backups. Use offsite or cloud storage with immutability, require MFA, and regularly test recovery.
- Create and practice an incident response plan. Quick action reduces downtime and cost.
- Conduct third-party security assessments. Outside experts can uncover vulnerabilities often overlooked internally.
- Train attorneys and staff. Regular phishing awareness and social engineering training helps prevent the human side of breaches.
Prevention is the Best Defense
Hackers know that law firms are rich targets with exploitable weaknesses. With double extortion, backup sabotage, and weak authentication, attackers are raising the stakes and the costs.
Firms that fail to act will remain vulnerable. Firms that invest in proactive security measures can protect client confidentiality, maintain compliance, and safeguard their reputation.
Don’t wait until your firm is the next target. Get your Free IT Assessment today.